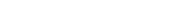Manage Relay and Routing Settings
This window controls the major features available on the Relay / Routing tab, and can be accessed by clicking the Add… button on the Relay / Routing tab. The features that are available on this window are described below.
Use DNS to resolve detination route
Selecting this option will make the recipients defined by the Email pattern or specific address field use standard DNS lookups to determine the mail server for recipients.
Route Description:
If you selected the Use DNS to resolve destination route field above, you must enter a description in this text field.
Forward to SMTP Server:
Selecting this option will make the recipients defined by the Email pattern or specific address field forcibly send their outbound SMTP messages to a specific SMTP Server. This selection will override the DNS lookup delivery method.
Send HELO insteand of EHLO
SMGW will use Enhanced SMTP syntax when supported by a destination mail server. For information regarding Enhanced SMTP syntax see RFC 3463. Select this option to override this behavior and default to standard SMTP.
Outbound Security
The Outbound Security button will open a new window that contains a variety of features to apply additional security. This is useful in the event that a mail server requires authentication before accepting the delivery of a message. The authentication options available are as follows:
Anonymous access
No authentication credentials will be supplied.
Basic Authentication
Requires that a User name and Password be supplied for the server to accept the message delivery. This information will be sent over clear text.
User name:
Enter the User name for Basic Authentication.
Password:
Enter the Password for Basic Authentication.
Use sender’s authentication
The credentials provided by the incoming connection will be used to authenticate to the destination mail server.
Deliver securely via TLS
TLS will be enabled on all connections being made to the server from which this window was opened. The server will make a number of attempts at these connections before sending via SecureMail. The number of attempts can be between one and ten, never, or forced to make the connection.
E-mail pattern or specific address:
For a route to take effect, the message recipient must be matched by one or more entries in the list. A specific email address can be any valid email entered in the standard “mail@mail.com” format. To enter a pattern into this field a “*” character (used to match one or more characters) and a “?” character (used to match a single character only) are required. The proper format for these characters is as follows:
*@bp1.com matches “joe@bp1.com” but not “joe@mail.bp1.com.”
*@mail?.bp1.com matches “joe@mail1.bp1.com” and “joe@mail2.bp1.com.”
Allow public relay to these entries.
If a computer’s IP address is allowed to connect to SMGW to send messages, but its IP address is not allowed to relay messages, you can still specify certain email addresses or patterns that can receive messages from this computer.
This setting can help prevent dictionary attacks if properly configured. In order to set up the configuration to use this feature, follow the steps listed below:
- Open the Properties of your virtual server and click on the Security tab.
- Click the Access Control button.
- In the Allowed Access tab click the Add button, and in the window that opens select the All Computers radio button.
- In the Security tab of your virtual server select the Relay / Routing Control button. Prevent all computers except your internal mail server(s) to relay messages through SMGW.
- To do this, select the Add button on the Allowed Relay tab. In the window that opens select the Single Computer radio button, and enter the IP Address of your internal mail server. Repeat as necessary for however many internal mail servers you have.
- Go to the Relay / Routing tab and select the Add button. In the window that opens enter your employees email addresses via the E-mail pattern or specific address: field. Repeat as necessary for however many employees you have (if you have a large number of employees, you can enter a pattern such as *@yourcompany.com to speed up this process).
- Place a checkbox in “Allow public relay to these entries.”
- Return to the Security tab and click the Spam Abuse Control button.
- Adjust the values of the Bad RCPTs per period before triggering abuse blocking (0=Off) field to block out bad RCPTs for a period of time.